
Weblog
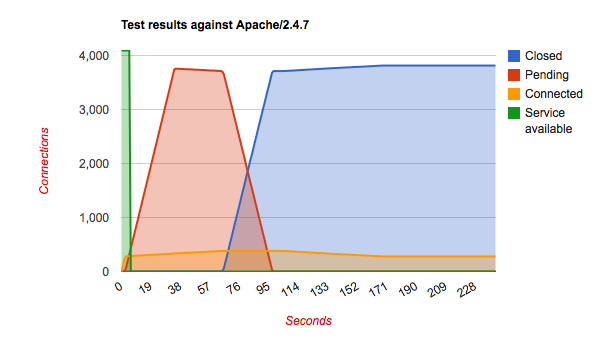
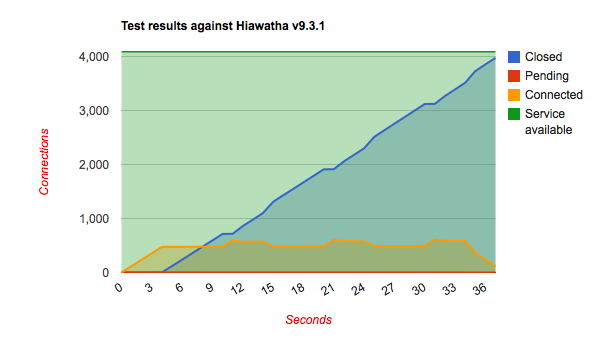
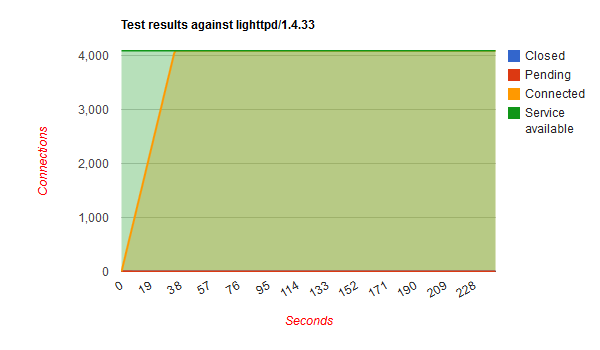
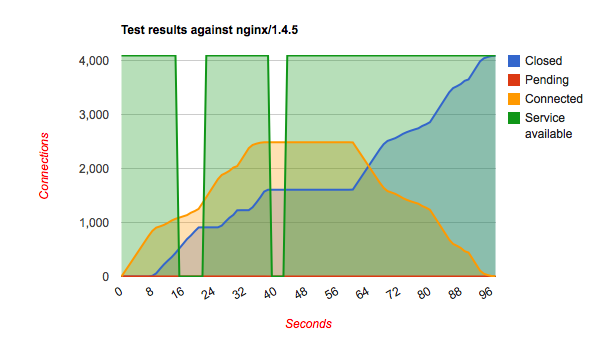
Chris Wadge has used the slowhttptest tool to see how well several (untuned) webservers are handling the slowloris attack. The results are quite interesting. I'll let them speak for themselves.
| Test parameters | |
|---|---|
| Test type | SLOW HEADERS |
| Number of connections | 4096 |
| Verb | GET |
| Content-Length header value | 4096 |
| Extra data max length | 52 |
| Interval between follow up data | 10 seconds |
| Connections per seconds | 128 |
| Timeout for probe connection | 3 |
| Target test duration | 240 seconds |
| Using proxy | no proxy |
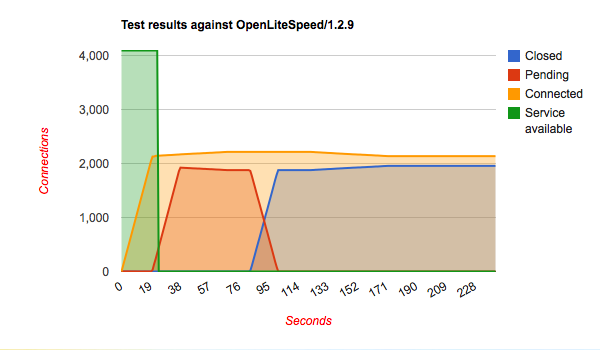
It's all about the green line and the required time to deal with the bad requests. It shows that Hiawatha stays available for other clients while under attack from one and deals with the attack more quickly than the other webservers. In other words, if you want sleep well at night knowing that your websites are online even while under attack, go for Hiawatha!
Cherokee crash
The Cherokee webserver was also tested. But because it crashed out of the box during the test, it didn't meet the tester's 'untuned' criteria, which was used for all of the other webservers featured.



Well done, I've always known you are the best. Simply the best!
I never doubted that Hiawatha is the best
the really confrontation are hiawatha vs lighttpd..
good work
Also, this not at all within the test parameters as I did some basic tuning, but for fun I cranked up both Hiawatha and the torture test to 11, so to speak. Gave Hiawatha a ConnectionsTotal and ConnectionsPerIP that was essentially limitless, and hit it with a 15-minute, high ramp-up SlowHTTPTest. In short, the results for the much smaller test seem to scale linearly [pub.dotbalm.org].